What is a Cross Site Request Forgery (CSRF)?
A CSRF is a type of exploit that a malicious website or attacker could employ to have a user send unauthorized commands to a website or application. It is a type of confused deputy attack against a user's web browser that tricks it to send malicious HTTP requests to a target website.
Some CSRF techniques are trivial to employ. For example, it is possible to place an arbitrary URL within an HTML IMG tag which will convince your browser to run an HTTP GET against that URL.
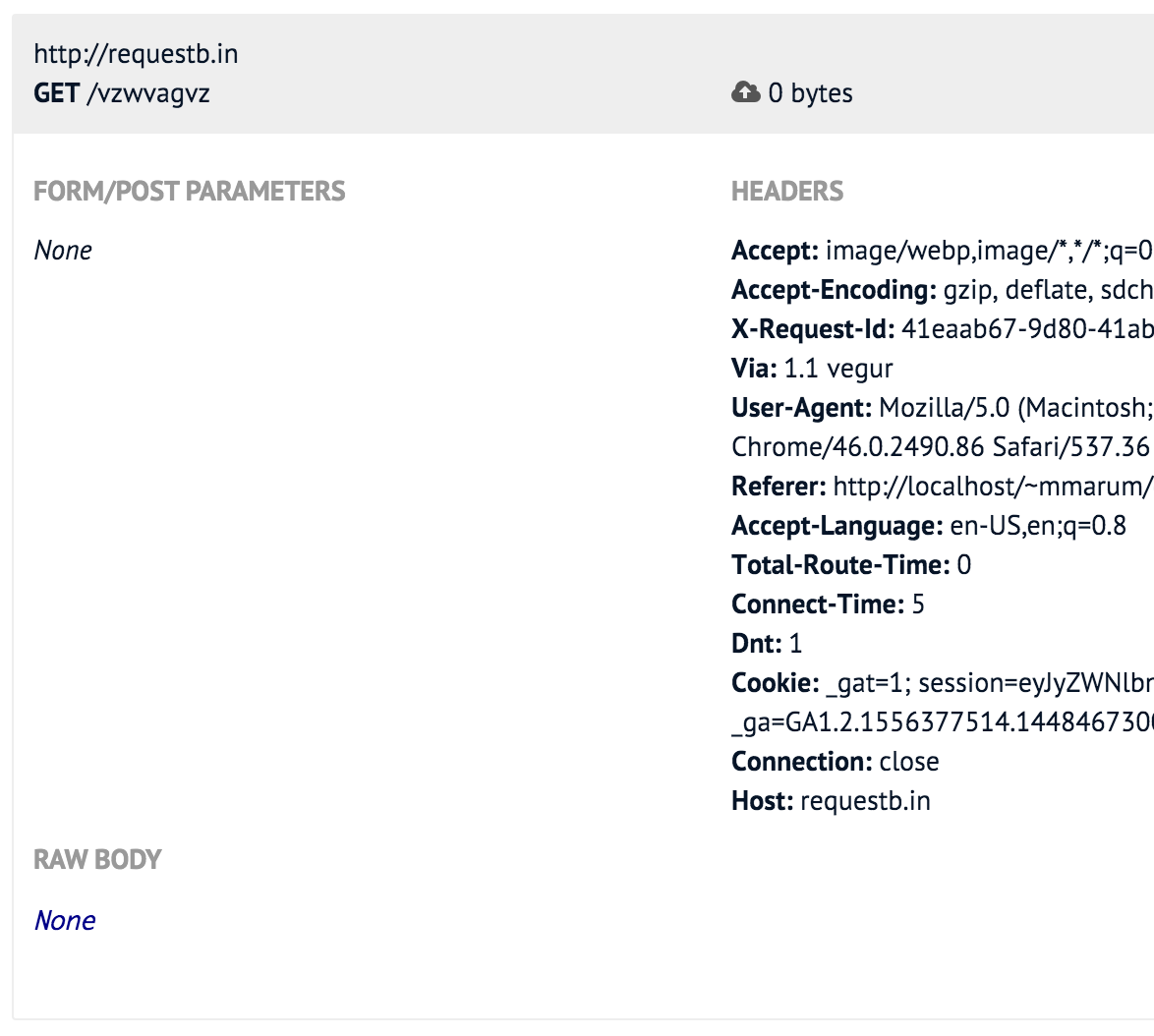
Try out this example that uses RequestBin. I added an image tag to a page in my local web setup.
<img src="http://requestb.in/vzwvagvz">
When I checked RequestBin then I could see what the request from my browser looked like to the external service.
A malicious HTTP GET can potentially expose sensitive information. For HTTP GET requests, the state of the system rarely changes meaning that lasting damage can be limited. What can be more troubling is when a browser is tricked into performing an HTTP POST using a maliciously designed HTML form.
CSRF Authenticator in Sugar 7.7
Here is some information from Jelle Vink (Security Architect) on the CSRF Authenticator added in Sugar 7.7. It is used primarily with Sugar 6.x based user interfaces (BWC modules) that include regular web forms since these are potential CSRF attack vectors. As of this writing, the Sugar 7.7 release is in beta.
Note that this is an early implementation and subject to change in future releases and therefore it is currently opt-in only for Sugar 7.7. But the CSRF Authenticator will be enabled by default in a later Sugar release.
CSRF Authenticator is not enabled by default in Sugar 7.7 but this will change in a later Sugar release!
This will affect the behavior of customizations made to BWC modules that generate HTML that includes web forms. There are actions that need to be taken to have these custom forms support CSRF authentication.
Enabling the CSRF Authenticator
To opt-in and enable this feature then use this directive in config_override.php:
$sugar_config['csrf']['opt_in'] = true;
How it works
We have added CSRF tokens to each web form that the Sugar application generates. If the correct token is not included during a form submit then the POST request will be rejected.
The Sugar 7.7 implementation ties the CSRF token used in BWC forms to the user's PHP session.
The SugarController class is used to determine if it is a modify action. When the SugarApplication class detects a modify action, the CSRF authentication logic in SugarController will be called for all POST requests.
For more details, see the SugarApplication and SugarController classes in the Sugar 7.7 codebase.
The following configuration parameters are available:
Soft Failure Mode
$sugar_config['csrf']['soft_fail_form'] = true/false
This config setting disables CSRF authentication and is only present to mitigate any upgrade issues where customizations are missing the necessary CSRF token inclusion.Using this settings is not recommended in a production environment! When soft failure is enabled then Sugar will merely log missing CSRF tokens or mismatches.
Token Size
$sugar_config['csrf']['token_size']
The size of the tokens (in characters) being generated. This value defaults to 32 characters.
Form Token Field
$sugar_config['csrf']['form_token_field']
This is the form field used to transport the token value. It defaults to 'csrf'.
Using the CSRF Authenticator
The CSRF Authenticator will be enabled by default in a future Sugar version. Developers should act now to make sure they are ready.Sugar Developers can enable CSRF authentication in Sugar 7.7 instances in their local development environment.config_override.php
$sugar_config['csrf']['opt_in'] = true;
Then you will see FATAL errors in the Sugar log when users use forms that do not have CSRF tokens added to them properly.sugarcrm.log
Wed Jul 1 06:47:46 2015 [710][1][FATAL] CSRF: attack vector detected, invalid form token detectedWed Jul 1 06:47:46 2015 [710][1][FATAL] CSRF: auth failure for Users -> Save
Sugar Developers should add the following Smarty tag to their custom forms used with BWC modules.
{sugar_csrf_form_token}For example,customform.tpl
<form name='myCustomForm' action="index.php" method="POST">{sugar_csrf_form_token}
<input type='hidden' name='id' value='{$id}'>
<input type='hidden' name='module' value='{$module}'>
...
</form>

-

SugarCRM Developers
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More Actions
-
Cancel
Comment-

SugarCRM Developers
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More Actions
-
Cancel
Children